Top Tech Companies (115)
Don't see your company?
Create a company profileThreat X is an information security start-up positioning itself to become the market leader in cyber security products and services. As attacks and threats evolve, most organizations are faced with high costs, stale technology and limited resources to combat malicious events. Built on Next-Generation technologies and techniques, ThreatX products arm organizations with enhanced situational awareness simplifying the path to threat neutralization.
SpyCloud is the leader in account takeover (ATO) prevention, protecting billions of consumer and employee accounts either directly or through product integrations. Our award-winning solutions proactively defeat fraud attempts and disrupt the criminals' ability to profit from stolen information.
Fifty years ago, Sam Walton started a single mom-and-pop shop and transformed it into the world’s biggest retailer. Since those founding days, one thing has remained consistent: our commitment to helping our customers save money so they can live better.
FormAssembly is an enterprise form platform built to help teams streamline complex processes and drive quality form conversions. We help organizations in healthcare, financial services, higher education and multiple other industries quickly create web forms, collect data, and streamline their workflows through smart integrations with Salesforce and other third-party systems.
Sevco Security is a company of cyber experts building services and products for cyber experts. Designing solutions to solve hard problem(s) associated with quickly discovering the context for who, what, where, why and how network connected devices relate on your network.
<p><span style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;">Quarri is a leading provider of on demand web information security solutions. Quarri Protect On Q protects information and content at the endpoint by enabling web security administrators to selectively secure and control to web sessions anytime, anywhere, without deploying client software. </span><br style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;"><br style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;"><span style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;">Quarri mitigates risk and maintains compliance with data leakage protection from user-based activities such as copying, printing, clipboarding or saving sensitive information, including from browser-launched processes like Adobe Acrobat or Microsoft Office. With no user installation, system modification, software installation or software left behind, Quari delivers significant deployment, support and usability cost savings. </span><br style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;"><br style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;"><span style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;">Quarri is a privately held, investor-backed corporation based in Austin, Texas.</span></p>
The security industry is in crisis. Rising costs continue to drive up the price of guarding even as quality declines. But, what if you could provide the same features as a human guard without the human? We will offer the first security solution based on emerging drone technology and our patent pending BaseStation at half the price of a human guard.
Whisel makes it easy to make responsible choices about personal security. Whisel is a network of trained and licensed personal security professionals who are on the ground in city neighborhoods. Coordinated through the Whisel app, our Security Partners are available to be there—at your side—just in case.
Williams & Wong is a boutique CPA firm, created to give the compliance and accounting industry a much needed face-lift. We provide accounting, audit, and compliance services to both startups and large public companies. We specialize in SOX, SOC, PCI, GDPR, and HIPAA regulations.
Most cybersecurity companies take a defensive approach — seeking to prevent known adversaries and cyber threats from penetrating your defenses. We play offense. Infocyte helps security teams proactively detect and respond to hidden and unknown threats (the sophisticated attacks that prevention and defensive tools are prone to miss).
Smarter Security is committed to providing premium solutions for life safety and entrance control. Intelligent and elegant Fastlane® optical turnstiles protect thousands of lobbies across six continents and are the world’s leading brand. Door Detective® provides tailgate detection and direction control for doors.
Safer Technologies formerly Campus Watch is a personal security platform that helps people access first responders when in danger. We serve a variety of commercial applications across multiple industries. We help companies bring better security to their human assets through aggregation and geolocation.
Ontic makes software that corporate and government security professionals use to proactively manage threats, mitigate risks, and make businesses stronger. Built by security and software professionals, the Ontic Platform connects and unifies critical data, business processes, and collaborators in one place, consolidating security intelligence and operations. We call this Connected Intelligence. Ontic serves corporate security teams across key functions, including intelligence, investigations, GSOC, executive protection, and security operations. For more information please visit ontic.co or follow us on X or LinkedIn.
Those who work for American Global Security have been trained to look for suspicious behavior, react quickly, and stop thieves in their tracks. They have the most comprehensive training in the business. American Global Security can help you with everything from general loss prevention services to complete loss prevention systems.
Experian has taken another important step in the transformation of its Consumer Services business, by acquiring CSID in August 2016. By bringing together Experian’s leading Consumer Services products with the proprietary technology of CSID’s identity protection platform, together we offer consumers and clients best-in-class credit and ID solutions.
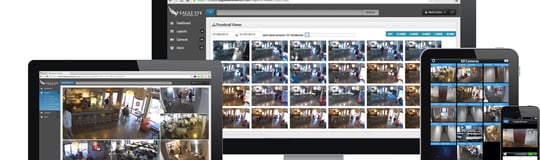
Eagle Eye Networks is #1 in cloud video surveillance worldwide. Our 100% cloud managed solutions provide cloud and on-premises recording, bank-level security and encryption, and broad analog and digital camera support – all accessed via the web or mobile applications. Businesses of all sizes and types utilize Eagle Eye solutions for operational optimization and security. All products benefit from Eagle Eye’s developer friendly RESTful API platform and Big Data Video Framework ™. Eagle Eye sells its products through authorized global resellers and installation partners. Headquartered in Austin, Texas, USA, Eagle Eye has offices in Europe and Asia-Pacific. For more information, please visit www.een.com
<p><span style="color: rgb(51, 51, 51); font-family: Helvetica, Arial, sans-serif; line-height: 17px;">Gazzang provides data security solutions and expertise to help enterprises protect sensitive information and maintain performance in big data and cloud environments. Our technology enables SaaS vendors, health care organizations, financial institutions, public sector agencies and more to meet regulatory compliance initiatives, secure personally identifiable information and prevent unauthorized access to sensitive data and systems. The company is headquartered in Austin, Texas and backed by Austin Ventures and Silver Creek Ventures.</span></p>
<p>MerlinCryption develops infrastructure security software, delivering advanced encryption, authentication, and random data generators, for Cloud, VoIP, eCommerce, M2M, and USB hardware. The company focuses in critical-need verticals, including financial services, healthcare, and military. <br><br>Forward-looking encryption technology secures data against the three known and critical risk factors, which are inherent in today’s encryption. Fortified with stealthy ASBE 2008 bit -2GB variable-key length cryptosystem, MerlinCryption solutions protect against current cyber threats, and position clients with their ‘next-generation security’ already in place. <br><br>The encryption defeats attack by cryptanalysis, incorporates passwords up to 64KB, and eliminates expensive PKI, which significantly decreases the cost and labor of key management. <br><br>Breakthrough embedded platforms and hardware protect the integrity of data-at-rest, data-in-motion, data-in-use, and data-in-change as it is created, viewed, edited, shared, stored, and moved across communications channels and in the Cloud. <br><br>The encryption is BIS approved for export, OFAC compliant, and enables clients with HIPAA and HITECH compliance. <br><br>MerlinCryption is headquartered in Austin, TX with east coast offices in New York City and Charleston, SC. The company is a Woman Owned Business. <br><br>MerlinCryption is changing the way the world protects data and secures connectivity</p>
<p><strong>BUSINESS SUMMARY</strong></p><p><strong>Scalar Security</strong> reduces the complexity around cybersecurity. We help companies identify big risks and conduct triage accordingly.</p><p> </p><p><strong>CUSTOMER PROBLEMS</strong></p><p><strong>1 |</strong> There are two types of firms: those who have been breached, and those who will be soon. Security programs are assembled <em>ad hoc</em> by managers who act hastily, not strategically. The byproduct is that cyber risks accumulate in blind corners, and wait.</p><p><strong>2 |</strong> All major insurers offer “cyber liability” insurance to cover a breach. They are accumulating – at portfolio level – the aggregated risks of their customers.</p><p style="margin-left:9.0pt;"> </p><p><strong>PRODUCT/SOLUTION</strong></p><p><strong><em>def.inity</em></strong> is a simple assessment that helps solution sellers and executives identify weak spots that represent big risks. The tool outputs non-technical reports that help the user make a business case for a targeted solution: an insurance policy, a technology product, or a consulting engagement.</p><p>This is beneficial <em>on the front lines</em> – for those attempting to implement firm-level solutions. The benefits accrue <em>at the macro level</em> – for insurance underwriters trying to structure their cyber risk into a profitable business.</p>
Transmute builds next-gen cloud-based identity management solutions for enterprises, leveraging blockchain technology to streamline and enforce identity authorization via key-based signatures, verifiable credentials, and immutable logging.



















.png)

.png)











.png)

